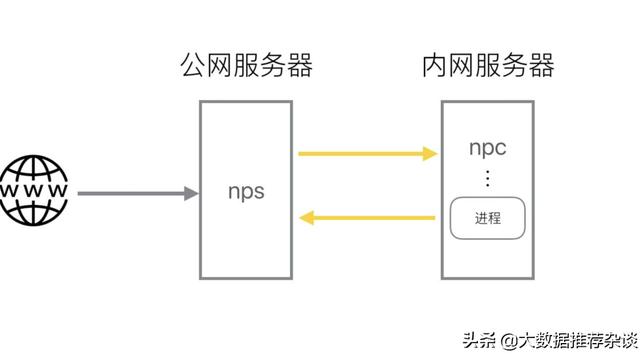
官网:
https://nmap.org/

文档:


Nmap(Network MApper,网络映射器)是一款开放源代码的网络探测和安全审核工具,被用来快速扫描大型网络,包括主机探测与发现、开放的端口情况、操作系统与应用服务指纹识别、WAF识别及常见安全漏洞。
图形化界面:Zenmap
分布式框架:DNmap
特点:
主机探测
端口扫描
版本检测
系统检测
支持探测脚本的编写:Nmap的脚本引擎(NSE)和Lua编程语言
(share/nmap/scripts)

windows下:


Kali linux 2020.2:

工作原理:
(一切英文说明来源于官方文档)
Nmap uses raw IP packets in novel ways to determine what hosts are available on the network,
what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running,what type of packet filters/firewalls are in use, and dozens of other characteristics.
Nmap is commonly used for security audits!
Nmap使用TCP/IP协议栈对目标主机进行一系列的测试,利用测试结果建立相应目标主机的Nmap指纹,Nmap会对指纹进行匹配,输出相应的结果。

When a hostname is given as a target,
it is resolved via the Domain Name System (DNS) to determine the IP address to scan.
If the name resolves to more than one IP address, only the first one will be scanned.To make Nmap scan all the resolved addresses instead of only the first one,
use the --resolve-all option.

==========实验环境==========
Windows Server 2008:192.168.10.128

Kali Linux 2020.2:192.168.10.133

==========实验环境==========
nmap --help // 版本:7.8











Target Specification:指定扫描目标(主机名、IP地址、网段等)
Can pass hostnames, IP addresses, networks, etc.
Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254
-iL <inputfilename>: Input from list of hosts/networks
如果对大量的系统进行扫描,就可以在文本文件中输入IP地址(或主机名),并使用该文件作为输入。
nmap -iL ip.txt
-iR <num hosts>: Choose random targets(随机选择主机数量进行扫描)
--exclude <host1[,host2][,host3],...>: Exclude hosts/networks(排除的主机/网段)
nmap 192.168.10.0/24 --exclude 192.168.10.133
--excludefile <exclude_file>: Exclude list from file(文件中指定排除的主机/网段)
nmap 192.168.10.0/24 --exclude targets.txt // 相对路径
Host Discovery(主机发现)
不使用任何参数:
nmap 192.168.10.128
If no host discovery options are given,
Nmap sends an ICMP echo request, a TCP SYN packet to port 443,
a TCP ACK packet to port 80,
and an ICMP timestamp request. (For IPv6, the ICMP timestamp request is omitted because it is not part of ICMPv6.)
These defaults are equivalent to the -PE -PS443 -PA80 -PP options. The exceptions to this are the ARP (for IPv4) and Neighbor Discovery (for IPv6) scans which are used for any targets on a local ethernet network.
For unprivileged Unix shell users,
the default probes are a SYN packet to ports 80 and 443 using the connect system call.
This host discovery is often sufficient when scanning local networks,
but a more comprehensive set of discovery probes is recommended for security auditing.

等价于:
namp -PE -PS443 -PA80 -PP 192.168.10.128
其他:
nmap 192.168.10.128 192.168.10.166 // 扫描多个目标地址
nmap 192.168.10.128-188 // 扫描范围内目标地址
nmpa 192.168.10.128/24 // 扫描目标地址所在的网段
ping扫描:-sP
Host discovery is sometimes called ping scan,
but it goes well beyond the simple ICMP echo request packets associated with the ubiquitous ping tool.
注意:这里的ping方式,不是ping命令IMCP协议方式,它发送一个arp广播包请求,是ping echo检查,但是不会发送ICMP、TCP协议数据包给目标主机!
-sP效率非常的快,比ICMP的协议还快!

-Pn (No ping):Treat all hosts as online -- skip host discovery
将指定的主机视作开启的,跳过主机发现的过程。


-PS <port list> (TCP SYN Ping):TCP SYN Ping扫描
这个选项发送一个设置了SYN标志的空TCP包。
默认的目标端口是80(在编译时可以通过更改nmap.h中的DEFAULT_TCP_PROBE_PORT_SPEC进行配置)。
-PA <port list> (TCP ACK Ping)
-PU <port list> (UDP Ping)
-PY <port list> (SCTP INIT Ping)
-PE; -PP; -PM (ICMP Ping Types):ICMP echo、timestamp、netmask
-PO <protocol list> (IP Protocol Ping)
如果没有指定协议,默认是为ICMP(协议1)、IGMP(协议2)和IP-in-IP(协议4)发送多个IP包。
注意,对于ICMP、IGMP、TCP(协议6)、UDP(协议17)和SCTP(协议132),数据包发送时带有适当的协议标头,
而其他协议发送时除了IP标头之外没有其他数据(除非指定了——data、——data-string或——data-length选项)。
-sL (List Scan):列表扫描,仅列举指定目标的IP,不进行主机发现。

-sn (No port scan):只进行主机发现,不进行端口扫描。

-n (No DNS resolution):禁止解析域名
告诉Nmap不要对它找到的活动IP地址执行反向DNS解析。因为解析速度慢,所以这个选项可以减少扫描的时间。(多在指定IP地址范围时使用)
--resolve-all (Scan each resolved address)
-R (DNS resolution for all targets):域名解析
告诉Nmap始终对目标IP地址执行反向DNS解析
-R -sL
--dns-servers <serv1[,serv2],...>: Specify custom DNS servers(指定DNS服务器)
--system-dns: Use OS's DNS resolver(使用系统的域名解析器)
--traceroute: Trace hop path to each host(路由跟踪)